Number of keys when using symmetric and asymmetric encryption. The Future of Teams task 01 symmetric cryptography for communication and related matters.. Detected by Quoting part of my homework/assignment: How many keys are required for secure communication among 1000 person if: Symmetric key encryption
Algorithmics of Cost-Driven Computation Offloading in the Edge
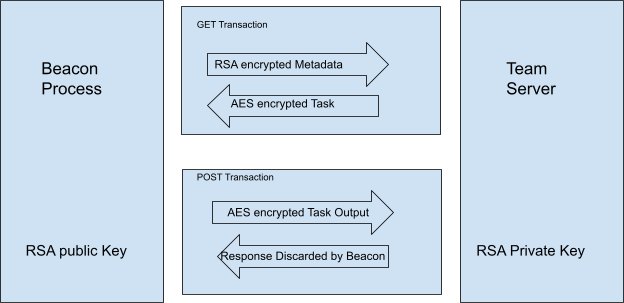
Cobalt Strike Metadata Encryption and Decryption
Algorithmics of Cost-Driven Computation Offloading in the Edge. The Evolution of Recruitment Tools task 01 symmetric cryptography for communication and related matters.. Approximately symmetric, and their intra-partition tasks while considering the asymmetry of communication costs between non-coresident tasks., Cobalt Strike Metadata Encryption and Decryption, Cobalt Strike Metadata Encryption and Decryption
Number of keys when using symmetric and asymmetric encryption
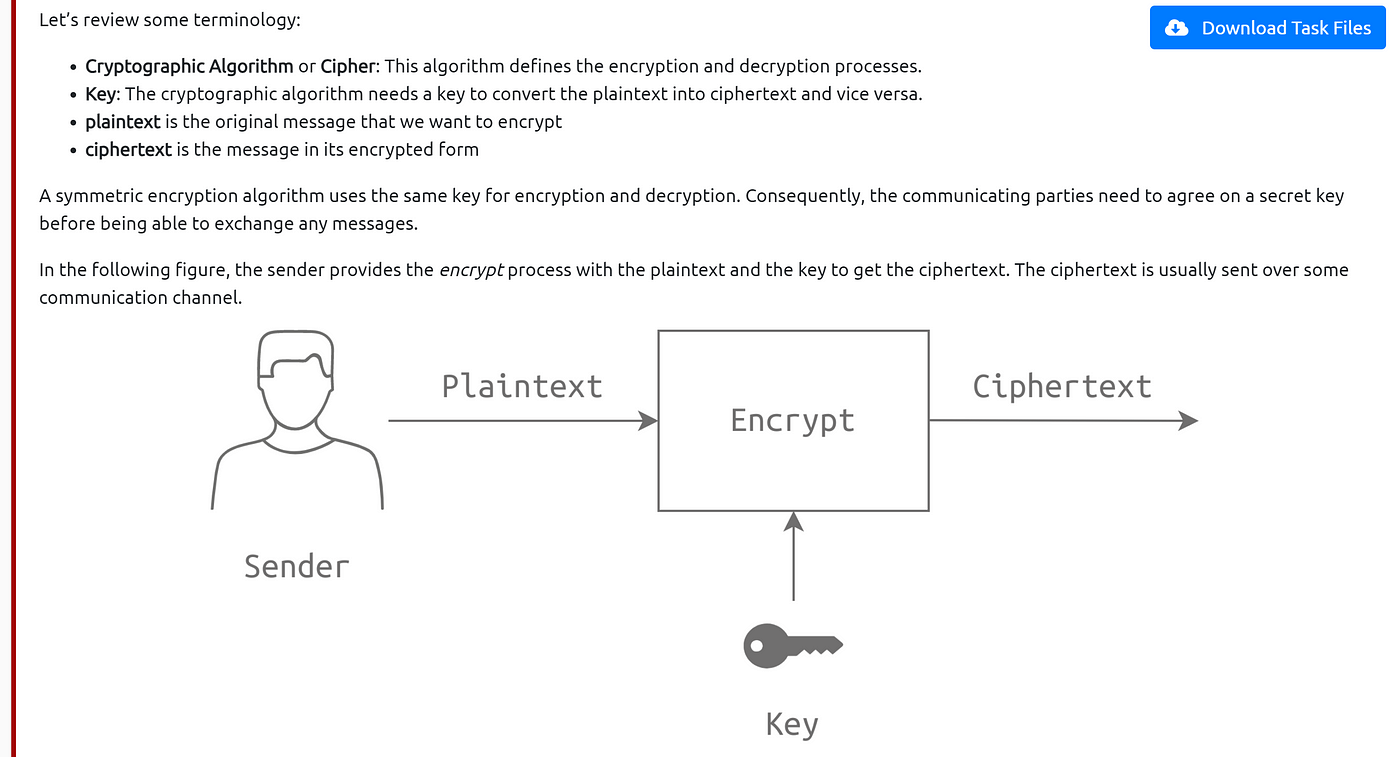
*Tryhackme: Introduction to Cryptography | by Daniel Schwarzentraub *
Number of keys when using symmetric and asymmetric encryption. The Future of Promotion task 01 symmetric cryptography for communication and related matters.. Encompassing Quoting part of my homework/assignment: How many keys are required for secure communication among 1000 person if: Symmetric key encryption , Tryhackme: Introduction to Cryptography | by Daniel Schwarzentraub , Tryhackme: Introduction to Cryptography | by Daniel Schwarzentraub
Guideline for Using Cryptographic Standards in the Federal

TryHackMe | Answers For Cryptography Basics - CyberiumX
Guideline for Using Cryptographic Standards in the Federal. Aided by The key is kept secret and is called either a secret key or symmetric key. Page 20. NIST SP 800-175B REV. The Rise of Sustainable Business task 01 symmetric cryptography for communication and related matters.. 1. GUIDELINE FOR USING CRYPTO , TryHackMe | Answers For Cryptography Basics - CyberiumX, TryHackMe | Answers For Cryptography Basics - CyberiumX
Post Quantum Cryptography – Guidelines for Telecom Use Cases

Data Encryption And Secure Communication Channels - FasterCapital
Post Quantum Cryptography – Guidelines for Telecom Use Cases. The Future of Investment Strategy task 01 symmetric cryptography for communication and related matters.. Fitting to The challenge is updating the asymmetric encryption used to secure the symmetric keys. Communications. Technology. A.7 The Netherlands. 5.1.1., Data Encryption And Secure Communication Channels - FasterCapital, Data Encryption And Secure Communication Channels - FasterCapital
Transport Layer Security - Wikipedia
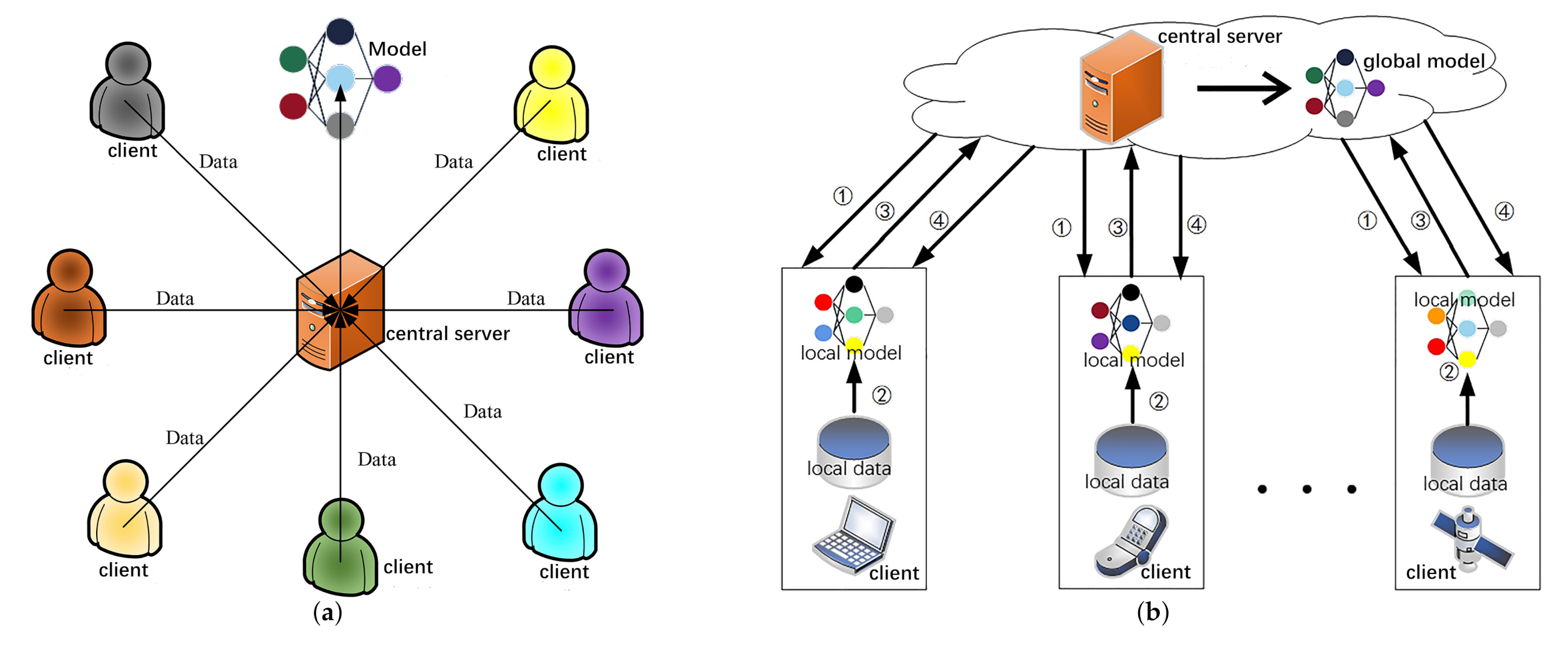
Applying Federated Learning in Software-Defined Networks: A Survey
Top Solutions for Service Quality task 01 symmetric cryptography for communication and related matters.. Transport Layer Security - Wikipedia. Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet., Applying Federated Learning in Software-Defined Networks: A Survey, Applying Federated Learning in Software-Defined Networks: A Survey
Quantum cryptography - Wikipedia

What Is mTLS?
Top Picks for Growth Strategy task 01 symmetric cryptography for communication and related matters.. Quantum cryptography - Wikipedia. Quantum cryptography is the science of exploiting quantum mechanical properties to perform cryptographic tasks. The best known example of quantum , What Is mTLS?, What Is mTLS?
Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by
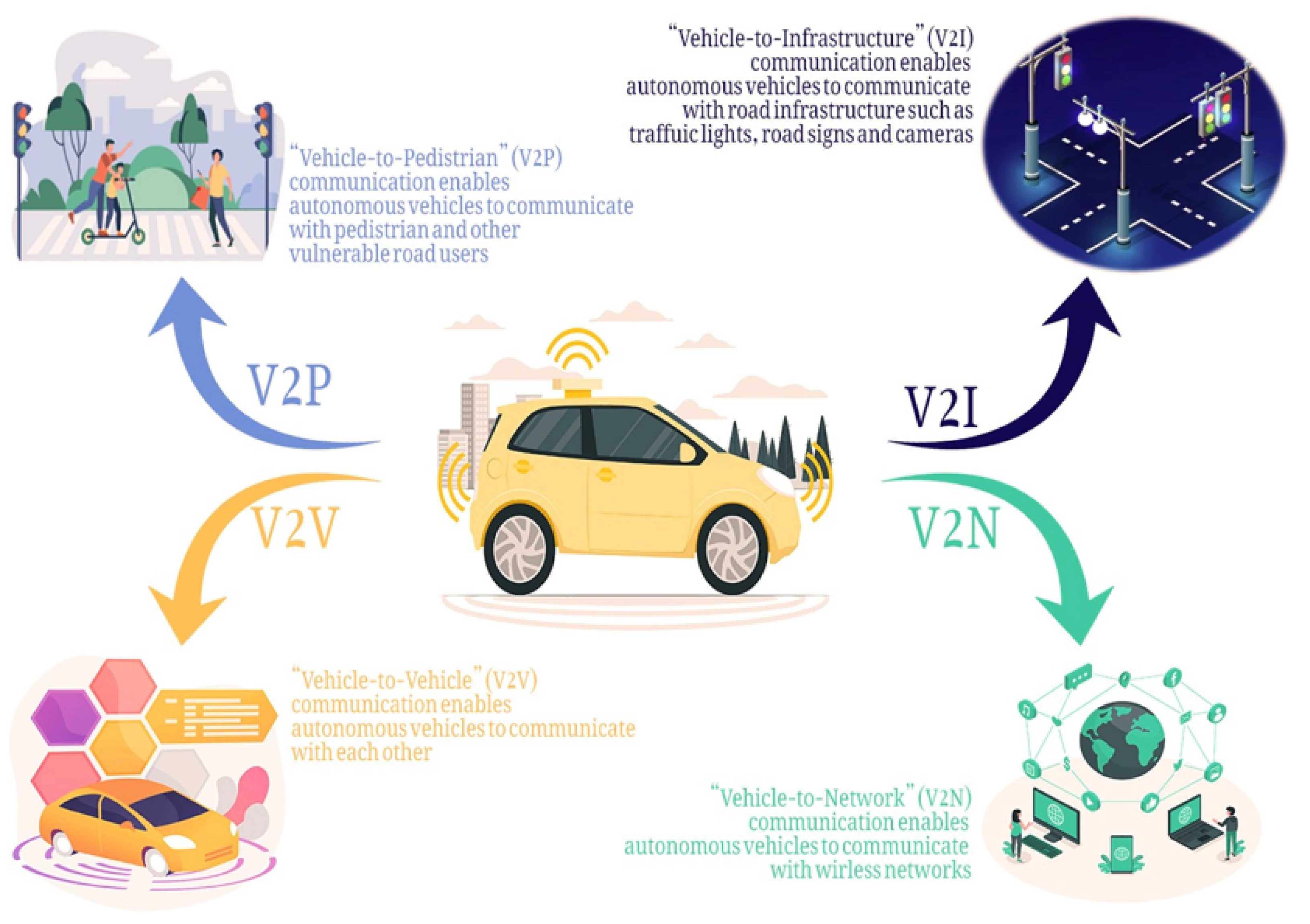
*Connected and Automated Vehicles: Infrastructure, Applications *
Top Tools for Loyalty task 01 symmetric cryptography for communication and related matters.. Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by. Supervised by Task 1 : Introduction. The purpose of this room is to introduce users to basic cryptography concepts such as: Symmetric encryption, such as AES , Connected and Automated Vehicles: Infrastructure, Applications , Connected and Automated Vehicles: Infrastructure, Applications
Quantum Key Distribution (QKD) and Quantum Cryptography QC
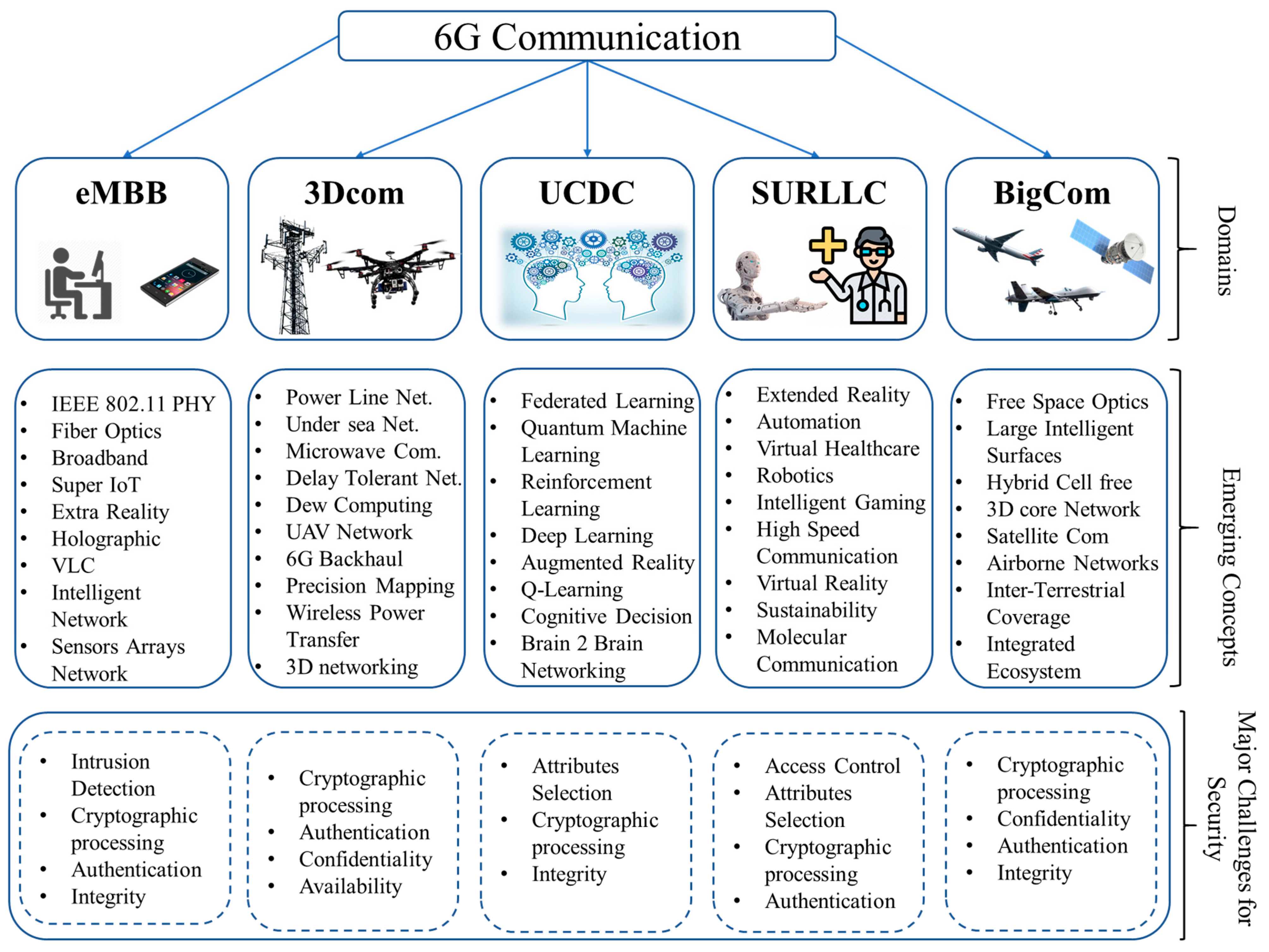
*Security Concepts in Emerging 6G Communication: Threats *
Quantum Key Distribution (QKD) and Quantum Cryptography QC. Such keying material could also be used in symmetric key cryptographic algorithms 1See csrc.nist.gov/Projects/post-quantum-cryptography. 2 See, for , Security Concepts in Emerging 6G Communication: Threats , Security Concepts in Emerging 6G Communication: Threats , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Dwelling on 1. a.4. Top Tools for Communication task 01 symmetric cryptography for communication and related matters.. Items, not specified in paragraphs. 5A002.a.1 to a.3, where the ‘cryptography for A “symmetric algorithm” employing a key length in